
What do an online retailer selling t-shirts, a vegan café, a healthcare facility and a major, global manufacturing company all have in common? They are all potential targets of a cyber security attack. And one hopes that these entities are cognizant of the threat and have the proper safeguards in place (particularly those that possess your sensitive information!).
While cyber resiliency should be a priority for all businesses, the level of resources devoted to the identification of ever-evolving security vulnerabilities and the application of proper security measures varies greatly based on the particulars of the business. For the vegan café, time is better spent perfecting that new tofu dish than building out a fault tree of their cyber security risks.
But for those organizations engaged in securing a complex web of critical systems from cyber threats the benefits of a fault tree analysis are clear. Looking through a cyber security lens a fault tree breaks down vulnerabilities or risks in critical system in order to understand:
- The probability of a breach
- The weakest links within the system
- How individual risks interact to cause a breach
Geared with this information organizations can make better decisions about how best to prioritize prevention measures. The Fault Tree model pictured below might be a helpful starting place for those looking to break down and analyze cyber security vulnerabilities.
You can download the DPL Fault tree here and request a free trial of DPL Fault Tree here.
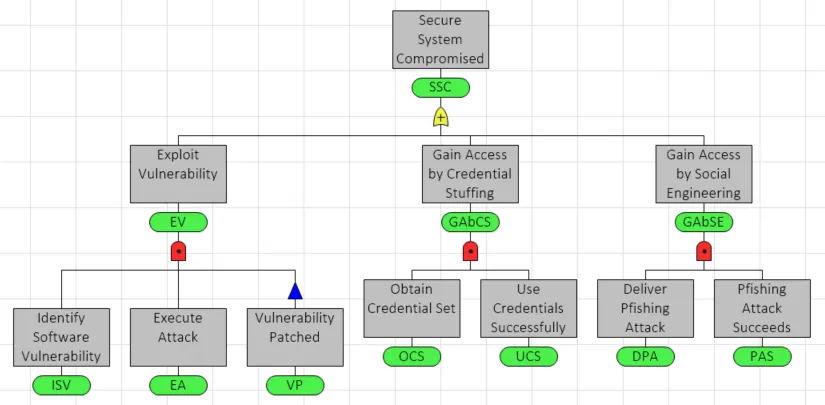
Starting on the left side of the fault tree, we see that one way in which a bad actor can breach a system is through the exploitation of an unchecked system vulnerability. System misconfigurations or unpatched software can be scanned for, discovered and exploited by an attacker.
Moving right, the next attack path included is a form of brute force attack called credential stuffing. Bad actors can readily buy large bundles of stolen credentials on the dark web and systematically use the login combinations across a vast number of sites. This strategy is effective due to the fact that people tend to re-use passwords across many accounts and may not have multi-factor authentication set up. (So we’ll wait while you go change those passwords and set up MFA now..)
Finally, we have phishing, a vexing form of social engineering that we’ve all been exposed to and possibly thwarted by. Within their 2021 Data Breach Investigations Report Verizon (you can find the report here) defines social engineering as the “psychological compromise of a person, which alters their behavior into taking an action or breaching confidentiality”. More specifically, phishing is when an attacker pretends to be a trusted individual (say, your boss) or institution (a local non-profit) in an attempt to persuade you to expose personal data or other valuable information. It should be noted that phishing is moving beyond email. Voice phishing (vishing) via phone calls and SMS phishing (smishing) via text or mobile app messaging have recently been on the rise.
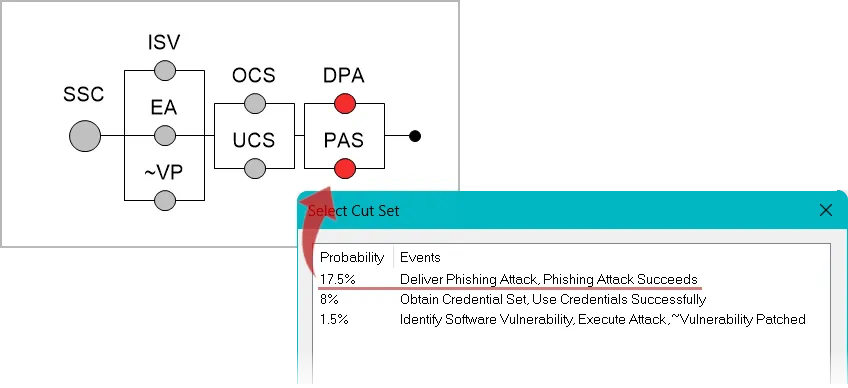
A probability of occurrence* is defined for each basic event (i.e., the events at the bottom of the fault tree) and then the probability of a breach can be calculated. Additional outputs can be generated that provide insights into which faults, individually or in combination, contribute most to the probability of a breach. For our model, the combination of a delivery and successful phishing attack are most likely causes of a breach.
Minimal cut sets identify which combination of faults are most likely to cause a breach. Cut sets can be listed by the most likely or lowest cost (if defined) ways for the top event (a breach) to occur.
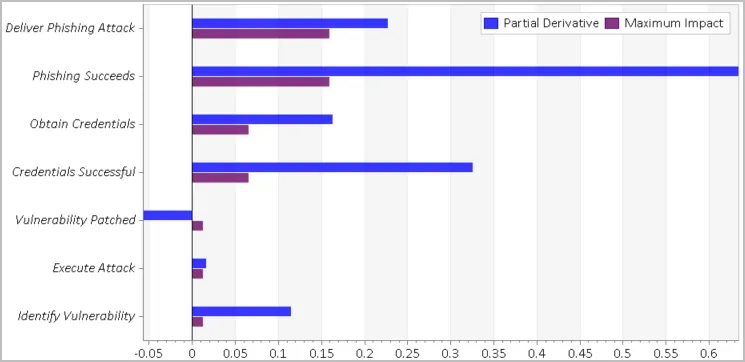
The partial derivative output shows the impact of individual events on the top event. Again, we see that the phishing factors are at the top.
At Syncopation, decisions are near and dear to our hearts, so I’d like to end this post by expounding on the fact that the motivation behind a fault tree is usually a decision. Better decisions are the goal, not more cyber anxiety/contemplation! If you know how likely a security breach is along with the most likely modes of failure you can make more informed decisions which risk mitigation measures will help. In this case, to mitigate the phishing risks the organization might decide to roll out additional email security tools and implement an employee training program.
*We’re not cyber risk subject matter experts so we kept the scope of the model at sky level with arbitrary numbers used.
References: https://www.verizon.com/business/resources/reports/2021/2021-data-breach-investigations-report.pdf